New (And Scary) Virus Has Popped Up – CryptoLocker
A new virus has shown itself in the form of what is called ransomware – a virus that claims to hold files or your whole computer under lock until you pay them a certain amount of money. The only difference with CryptoLocker than what we’ve seen before? It actually does hold your files under a secret lock and key and will not let it go unless you pay the price.*
Getting this virus can vary but most of the time it comes in an email attachment. Unfortunately one of our customers got it by opening up an email from “her bank” with an attachment. She ran the executable file (.exe) that was included. Afterwards when she tried to go to her bank’s website, it asked for more information than normal like her driver’s license number and credit card information. That’s when she got suspicious and called her bank and they let her know that they never ask for that information online. We don’t know if these are related or not, but it never hurts to re-illiterate to never open up unknown/unexpected email attachments.
Shortly afterwards a popup appeared that looked like 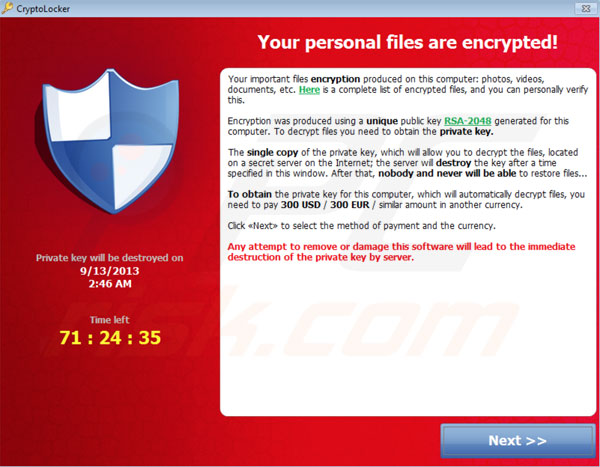 this:
this:
Here’s what we know so far:
- Yes, the files really are encrypted
- Many if not all personal files (.doc .xls .ppt .eps .ai .jpg .srw .cer) become locked out – for most home computer users this affects Microsoft Office Documents and picture files
- The virus scans the entire system and encrypts shared server folders and attached hard drives (including external drives)
- If you have online backup that detects and uploads files that have been changed, chances are that the encrypted files have been uploaded to your latest backup
- Paying the ransom is (sadly) an option, but there is still a chance that your files won’t be unlocked
- Finally, the virus can be removed but so far no one has figured out a way to decrypt the files
This is a really scary virus and unlike the FBI/DOJ/ICE/MoneyPak ransomware virus it actually does what it says.
Avoid the virus by using basic precaution when surfing the web and using email:
- Make sure your computer is fully updated (this includes Windows Update, your anti-virus, Java, Flash, etc.)
- Don’t visit websites that you don’t know about
- Don’t open unknown/unexpected email attachments (when there’s any doubt, email the person back and ask if they meant to send it or call the company to verify)
- Backup your computer to an offline external source and make sure it’s detached unless you’re doing a backup
If you have any questions, feel free to contact us and we’ll be happy to help. Unfortunately right now there truly is no way to get the files back – and lots of encryption experts are trying to figure it out.
* There have been reports of users who have paid the ransom and had their files decrypted – on the other hand others have paid and been left in the rain.
***Update: There is a possibility that we will be able to retrieve the files to where they were before they have been encrypted. Although we would be able to confirm over the phone if you have this virus, we wouldn’t know if we could retrieve your files until your computer is in our shop.



